1. [PDF] Data Spills - CDSE
Jun 18, 2018 · Screen Text/Images: A data spill incident is when classified data is introduced to an unclassified computer system or a system authorized at a ...
2. Data Spill - CyberHoot Cyber Library
Aug 16, 2020 · A Data Spill, or Data Leak, is the accidental or deliberate exposure of information into an unauthorized environment. Data spillage is often ...
A Data Spill, or Data Leak, is the accidental or deliberate exposure of information into an unauthorized environment.

3. What is Data Spillage? - StorageReview.com
Aug 27, 2019 · Data spillage occurs when sensitive, confidential, or malicious information is movemed into an environment not authorized to possess or view ...
Data spillage occurs when sensitive, confidential, or malicious information is movemed into an environment not…
4. Data Spill – An Everyday Threat to National Security
Aug 16, 2019 · In national security spaces, classified data can end up on unclassified or lower-level classification systems. This is known as a data spill.
By Michael Waksman, CEO, Jetico Inc. Oy Data has a frequent troublesome habit of residing somewhere it shouldn't. In national security spaces, classified data can end up on unclassified or lower-level classification systems. This is

5. What is Data Spillage | Centraleyes
NIST defines data spillage as a “security incident that results in the transfer of classified information onto an information system not authorized to store or ...
Data spills are on the rise, and they can wreak havoc on any organization. From damaged reputations to financial losses, the consequences can be severe.
6. data spillage - Glossary | CSRC - Computer Security Resource Center
Security incident that results in the transfer of classified information onto an information system not authorized to store or process that information. Source( ...
Search
7. What is a Data Spillage? - Medium
Jun 2, 2022 · The primary cause of a data leak is often negligence, ineptitude, or other human error. Often, there is no malice (the data is revealed by ...
There is a risk of data leakage when sensitive, confidential, or harmful information is moved into an environment where it is not permitted…

8. Data Spills - Security Awareness Hub
Skip to Content. DOD Logo. Exit Button EXIT Menu Button MENU. Data Spills. Introduction. d. Close CC Button. Closed Captions Transcript.
Skip to Content
9. Cyber Security Solutions: Data Spillage and How to Create an After ...
Jan 4, 2016 · The term “data spill,” according to the National Security Agency, refers to the “transfer of classified or sensitive information to unaccredited ...
Photo courtesy of Center for American Progress Action Fund(CC No Derivatives) Cyber Security Solutions: Data Spillage and How to Create an After-Incident “To Do” List President Obama and China’s President Xi Jinping “understanding” about cyber theft in their recent meeting stirs up worries about company data being compromised. Unfortunately, there’s nothing you can do if...

10. 5 Data Spill Management Tactics - The Manifest
Nov 2, 2021 · A data spill occurs when a breach results in a loss of data. Management tactics can prevent significant loss and help you recover quickly ...
A data spill occurs when a breach results in a loss of data. Management tactics can prevent significant loss and help you recover quickly from an attack.
11. A data spill (Classified Message Incident (CMI)) procedure or policy ...
Sep 21, 2012 · Description. When a data spill occurs on a smartphone/tablet, classified or sensitive data must be protected to prevent disclosure.
Security Technical Implementation Guides (STIGs) that provides a methodology for standardized secure installation and maintenance of DOD IA and IA-enabled devices and systems.
12. Steps to address data spillage in the cloud (ITSAP.50.112)
Sep 23, 2019 · Data spillage occurs when sensitive information is placed on information systems that are not authorized to process or store the information or ...
Steps to address data spillage in the cloud (ITSAP.50.112)

13. Data Protection – Part 1: ACSC's Data Spill Management Guide - LinkedIn
Jun 16, 2020 · DLP is a term encompassing the array of tools and processes used by cyber security practitioners and support staff to prevent sensitive data ...
Introduction Every organisation fears losing its critical, confidential, highly restricted or proprietary data. No points for guessing that one.

14. A Complete Guide to Managing Data Spills - Shred Cube
Nov 20, 2020 · The National Institute of Standards and Technology (NIST) defines a data spill as a “security incident that results in the transfer of ...
Has your company ever experienced a data spill, or would it even know if it had experienced one? Here is a complete guide to managing data spills. Read more.

15. Data Spills Definition | Law Insider
Data Spills means data (including classified information) authorized to be accessible to a selected audience that has become available to unauthorized persons.
Sample Contracts and Business Agreements

16. [PDF] Data Spill Cleanup - What's SSD Got To Do With It?
files + all data remanence beyond forensic recovery. • Data Spill clean-up. BCWipe Total WipeOut. • Erase entire drives for disposal or repurpose. DoD-Approved ...
17. [PDF] Spillage of Classified Information onto Unclassified Systems Procedure
Aug 29, 2019 · per EPA Information Security – Incident Response procedures. b) The CC shall open a CSIRC security incident ticket containing the terms. “ ...
18. Data Spill Lessons From the Oil Industry - ISACA
Historically, data management was a money outflow for organizations; the primary expense was allocated to data archival to comply with regulatory ...
Historically, data management was a money outflow for organizations; the primary expense was allocated to data archival to comply with regulatory requirements.

19. Data Security 101: What Is Data Spillage? - Bootstrap Business
Illegal activity aside, data spillage happens when confidential information finds its way to another location where unauthorized individuals can gain access.
What is classified as data spillage? How does a data spill commonly occur? Read on to learn everything you need to know about information leaks here.

20. Washington's little secret: 'Spillage' of classified information is a common ...
Jan 19, 2023 · (CNN) — A Defense Department contractor allowed classified information to sit unprotected in a commercial cloud and email server for nearly ...
(CNN) — A Defense Department contractor allowed classified information to sit unprotected in a commercial cloud and email server for nearly two years. A private attorney received a 1,000-page file from the Army as part of litigation — only to be asked to return it to a special courier several weeks later because it contained […]

21. [PDF] Unauthorized Disclosure of Classified Information for DoD and Industry
Unauthorized disclosure of classified information is a type of security incident that can be characterized as an infraction or violation depending on the ...
22. Input of sensitive corporate data into ChatGPT 2023 - Statista
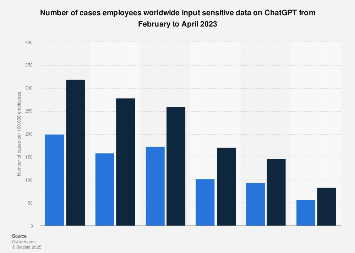
Jun 22, 2023 · Global cases of sensitive data spill into ChatGPT 2023 ... Between the 9th and 15th of April 2023, per 100,000 employees, 319 cases of sensitive ...
Between the 9th and 15th of April 2023, per 100,000 employees, 319 cases of sensitive data leaking on ChatGPT were spotted in worldwide companies.
23. Clubhouse confirms data spillage of its audio streams - BBC News
Feb 24, 2021 · A data spillage, on the other hand, is an incident whereby confidential information is released into an environment that is not authorised to ...
A user has been banned for streaming audio from multiple Clubhouse chatrooms onto their website.
24. Spill Incidents | State of New York
Skip to Main Content. DATA.NY.GOV · Sign In. English. English · Español · Italiano · Français · 中文 · Русский. Search Search. OPEN NYCATALOGDEVELOPERS.
OPEN NYCATALOGDEVELOPERS